This article describes how to provision LUSID using SCIM when Okta is your identity provider. After you configure SCIM provisioning, you can manage LUSID user attributes and group memberships from Okta. More about SSO.
A SCIM provisioning setup for LUSID using Okta supports the following features:
Push Users: Users in Okta that are assigned to the LUSID application in Okta are automatically added as members to your domain in LUSID.
Update User Attributes: User attributes that are updated in Okta are automatically updated in LUSID.
Deactivate Users: Users that are deactivated in Okta are automatically deactivated in LUSID.
Import Users: Users created in LUSID can be imported into Okta and either matched against existing Okta users or created as new Okta users.
Push Groups: Groups and their members in Okta can be pushed to LUSID as LUSID roles.
Import Groups: Import roles from LUSID as groups in Okta. Note that Okta does not allow you to manage memberships of these imported groups.
Profile Sourcing: Allows LUSID to be a source for user profiles.
LUSID does not currently support the following Okta features:
Sync Password
Prerequisites
You must be assigned the required licences to use SCIM provisioning. To request these licences, contact Technical Support.
Enabling SCIM provisioning in LUSID
To enable SCIM provisioning in LUSID, call the AddScim API. The example below shows a typical curl request where <your-API-access-token> is your generated API access token.
The response contains the base URL and API token you must enter into Okta (see section below).
Enabling SCIM API integration in Okta
To enable SCIM API integration in Okta:
Log in to your Okta Admin dashboard and then add the LUSID application.
From the application, click the Provisioning tab and then click Configure API Integration:
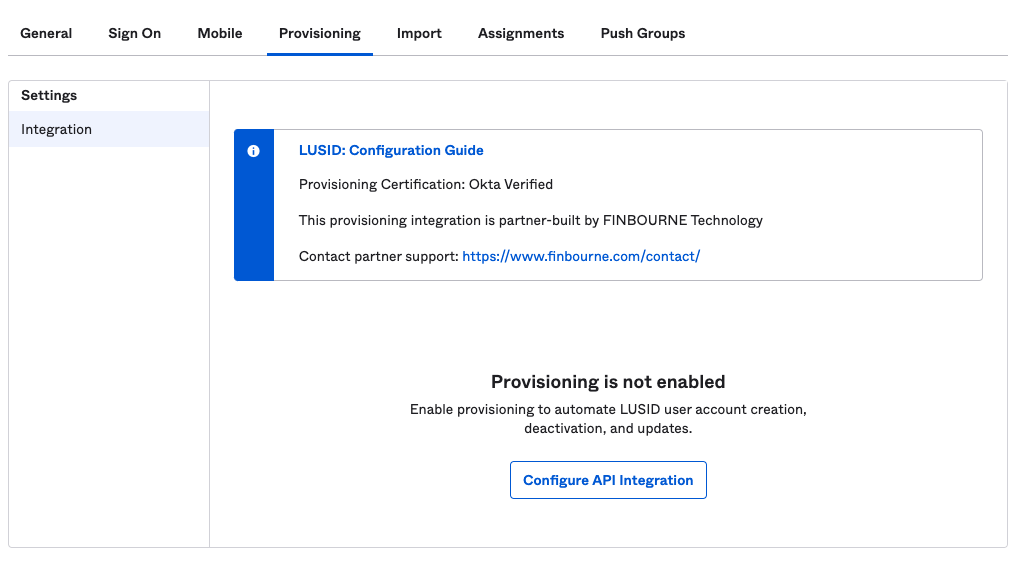
Select Enable API Integration.
Enter the base URL and API token that were generated from the request to AddScim (see above):

Click Test API Credentials. If the test passes, click Save.
Click To App under SETTINGS.
Click Edit and select Enable for the features you want to use:
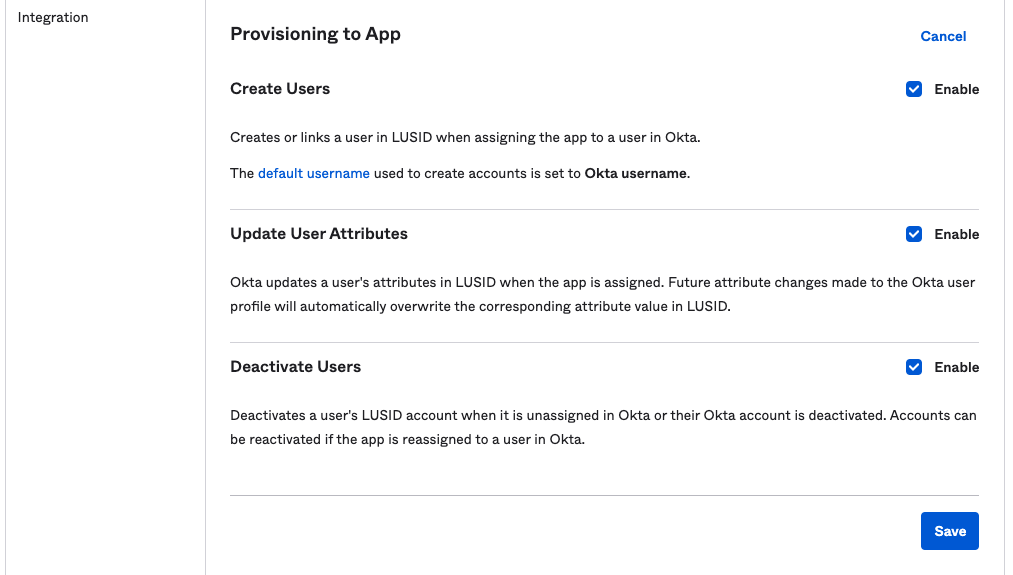
Click Save.
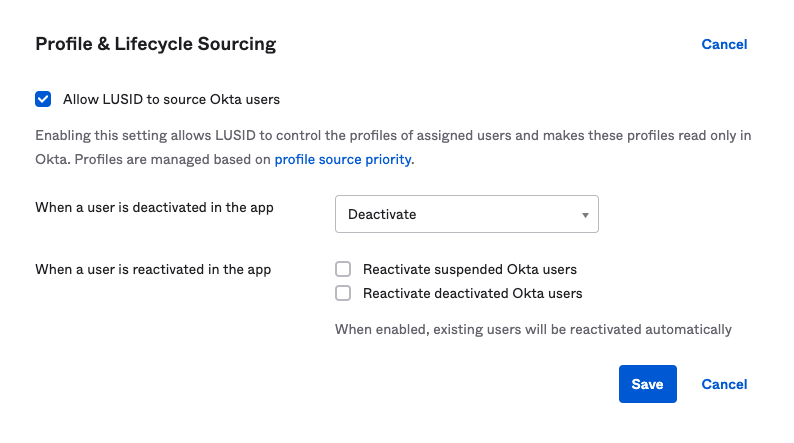
If Profile Sourcing is required, click To Okta, scroll down to Profile & Lifecycle Sourcing, click Edit and then configure the settings that you require:
Troubleshooting
Groups as roles
Groups that are synced with LUSID via SCIM will appear as roles within LUSID's Identity service. These roles must be manually created within LUSID's Access service, and policies assigned to them. This can be done using the Identity and Access > Roles dashboard within the LUSID web app, or programmatically via the Access API.
Contact
If you have any questions or difficulties with your LUSID SCIM integration, contact Technical Support.
